
When was the last time you cleaned your computer? Did you know that most computers are filled with unneeded files and programs and contain viruses, malware, and even more spyware? If you have ever wondered what exactly a M_agent _Service is or how you can clean it out of your computer, then read on.
This article offers information on what M_agent _Service is, where it comes from and how to remove it from your computer or tablet. It also contains tips on how to maintain your computer so this problem never arises again.
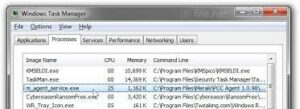
What Does It Do?
Several antivirus tools, including Bitdefender and Kaspersky, identify m_agent _service as a ransomware program. Ransomware works by locking down files on your computer that you need to use daily.
In most cases, it’s possible to recover those files, but it will cost you. A 2016 study from Sophos showed that nearly half of small businesses surveyed had paid a ransom at some point in their careers; 32 percent said they had been hit by ransomware in just six months.
Is It safe?
It may seem like there’s an antivirus program for every possible circumstance, but some programs can actually be more harmful than helpful. That’s especially true if you install an anti-malware program (or a PUP, or potentially unwanted program) that doesn’t work properly.
Let’s look at what these types of software are and how to know if you should keep it on your computer. If you do, make sure it’s up to date! In general: When deciding whether or not an application is safe, consider its source.
Make sure you trust the developer—if something seems suspicious about where it came from, don’t download and run it.
As with any other piece of software, scan it before installing to make sure that nothing malicious is attached—and always update regularly! Don’t rely on one tool: The best way to protect yourself from malware is to have multiple layers of protection in place.
Keep your operating system updated, use common sense when downloading files, use strong passwords and two-factor authentication wherever possible, and try out some free anti-malware tools such as Avast or Malwarebytes Anti-Malware. You might also want to consider a paid security suite such as McAfee AntiVirus Plus.
Removing/disabling M_agent _Service
To remove m_agent _service you will need to follow these instructions. You should also scan your computer for viruses, as it may be a virus pretending to be m_agent _service.
To do so, please use your favorite antivirus software and scan your computer for viruses. If you don’t have any anti-virus software installed on your computer yet, we highly recommend downloading one of these free programs: AVG AntiVirus Free Edition, BitDefender AntiVirus Plus, or Kaspersky Anti-Virus.
Be sure to scan your computer after disabling the m_agent _service and removing it from your system.
We suggest scanning with at least two different anti-virus programs just to make sure that there is no other viruses/malware on your system before you continue using it.
Signs Of A Malware Infection
Malware can take many forms, and it’s often difficult to tell if you have an infection. Here are some common symptoms of a malware infection.
If you see any of these signs, run your antivirus software immediately. If that doesn’t work, consider investing in another security program like Malwarebytes Anti-Malware (for Mac) or HitmanPro (for Windows).
These programs are designed specifically for malware removal and should be more effective than your standard antivirus toolkit. Prevention: In general, it’s best not to download anything from unknown sources—even if they appear safe at first glance.
Even major websites can unknowingly host malicious files on their servers; they just may not realize it yet! Use trusted sources when downloading files such as torrents and don’t click links unless you know where they lead.
Finally, make sure all your software is up to date. Outdated operating systems and applications are particularly vulnerable to attacks because they may not have been updated with new patches that close known vulnerabilities.
And remember to always use two-factor authentication whenever possible. It will add another layer of protection between you and potential hackers by requiring them to have both your password and access to your phone before they can log into an account.
Google Authenticator (Android iOS) is a great option for two-factor authentication, but there are other services out there too such as Duo Mobile and Authy. You might also want to consider using a VPN service like NordVPN.
A virtual private network creates an encrypted tunnel between your computer and a server operated by your VPN provider. All data traveling between your device and the server is unreadable to anyone else because it’s encrypted.
This includes, crucially, your ISP—which means that even if someone were to intercept traffic from your connection, they wouldn’t be able to view its contents without decrypting it first.
Five Types Of Computer Virus
The term computer virus covers a broad range of malicious programs that are intended to damage or disable computers, networks, and/or electronic devices.
It’s important to be able to identify what type of virus you’re dealing with so you can stop it before it becomes a bigger problem for your network.
Here are five types of computer viruses boot sector viruses; data-destroying viruses; trojans; worms; and macro viruses. Each type comes in different shapes and sizes but has one thing in common: they all need to replicate in order to do any real harm.
When they spread from one machine to another they can wreak havoc on both individual machines as well as on entire networks.
If you want to keep your company safe from these destructive malware attacks, make sure you have an anti-virus software solution that’s updated regularly.
And remember—it takes more than just anti-virus protection to protect yourself against today’s sophisticated malware attacks.
You also need backup solutions and other security tools like firewalls and intrusion prevention systems (IPS). Make sure you have a complete defense strategy by checking out our Security Solutions Center.
Conclusion
While malware and virus scanners should be a standard security measure for all users, it can be difficult to determine which applications are trustworthy.
If you have been infected with a virus from an unrecognized application, run a scan on your system immediately.
You may not know what M_agent _Service is; however, you do know that it’s something that shouldn’t be running in your system. The best way to ensure it doesn’t return is to make sure all applications are legitimate.




Leave a Reply